
Self signed certificates comes handy if you are a developer or tester when you are testing application. In the Windows 10 and older platforms, simply importing the self signed certificate into the trusted root certificate folder in the client machine used to trust the self signed certificate. However, during one of my tests today, Windows 11 was not trusting the certificate even though the certificate existed in Trusted root folder of the client machine. Both google chrome and Edge was showing the certificate was untrusted. I almost spend 2 hours breaking my head diagnosing the issue.
Then I went to the basics, reading the error messages completely. I could see that there was an error message that I ignored. It read something name hostname doesn’t exist in the subject alternate name of the certificate. When I dissected the self signed certificate, unlike in the below screen the subject alternate name field was completely missing in the original certificate we used.
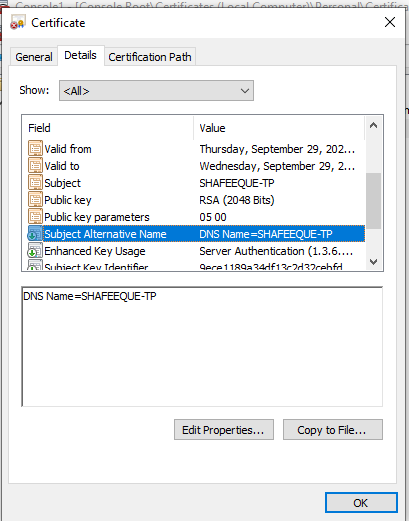
I wanted to find the root cause of the issue and wanted to find how this self signed certificate was generated. The certificate was generated through IIS Manager using “Create Self Signed Certificate” function.

If you plan to use the self signed certificate, try not to use the IIS manager to generate self signed certificate. Instead use New-SelfSignedCertificate module in PowerShell which i have explained in detail in my below post.